PIM ID authentication
Authentication
Authentication is the process of proving your identity to the system. The KPN Developer Portal uses the OAuth 2.0 Client Credentials Grant type: Client ID and Client secret.
To use the KPN APIs, you must obtain an access token (also called bearer token) by invoking our Authorization API using a POST method and sending the client credentials in the request.
URL: https://api-prd.kpn.com/oauth/client_credential/accesstoken?grant_type=client_credentials
Authentication workflow
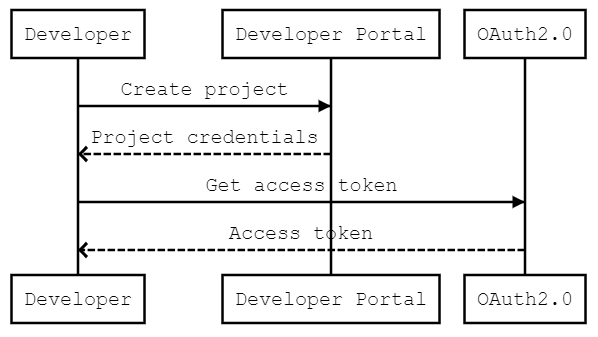
Where can I find my client credentials
Login into the My Developer Portal.
- Project: Click on a project in Projects to see your
Client IDandClient secretfor all APIs in that project. Use these credentials for your production applications.
Use them for authorization in SwaggerHub or when you send an API request to the KPN Developer Portal, for example with Postman or in a cURL request. You will receive an access token in the JSON message body of the response.
For example: "access_token": "haf2SDl07E9N7RluNQ4kJ1TkGgso".
Authenticating using cURL
Execute the cURL command to receive an access token. Replace APP_CLIENT_ID and APP_CLIENT_SECRET with your credentials (Client ID and Client secret).
cURL for Linux and MacOS
Code copied curl -X POST \ 'https://api-prd.kpn.com/oauth/client_credential/accesstoken?grant_type=client_credentials' \ -H 'content-type: application/x-www-form-urlencoded' \ -d 'client_id=APP_CLIENT_ID&client_secret=APP_CLIENT_SECRET'cURL for Windows
If you are using cURL for Windows, please use the command below instead.
Code copied curl -X POST "https://api-prd.kpn.com/oauth/client_credential/accesstoken?grant_type=client_credentials" -H "content-type: application/x-www-form-urlencoded" -d "client_id=APP_CLIENT_ID&client_secret=APP_CLIENT_SECRET"Response
The authentication service returns a JSON message that contains the access_token field.
Code copied Successful HTTP Status: 200{ "refresh_token_expires_in": "0", "api_product_list": "[xxxxxx]", "organization_name": "kpn", "developer_email": "demo123@kpn.com", "token_type": "Bearer", "issued_at": "1587458037687", "client_id": "APP_CLIENT_ID", "access_token": "staG765sBUuai4OMeZiTful6PTRt", "application_name": "test_application", "level": "demo", "scope": "", "expires_in": "3599", "refresh_token": "", "refresh_count": "0", "status": "approved"}Run this endpoint
You can easily run this and other endpoints.
- Go to the API on SwaggerHub.
- Click Authorize.
- Enter your
client_idandclient_secretusing your KPN Developer Portal credentials (Client IDandClient secret). - Click Authorize.
- Click Close.
- Click an endpoint.
- Click Try it out.
- Enter/select all required parameter values and any optional parameter values.
- At the bottom of the form, click Execute.
Review the Response.
Authenticating using SwaggerHub
- Open the API reference of the API you want to use.
- Click on the
Authorizebutton on the right. - In the form, fill in
client_idandclient_secret, using your KPN Developer Portal credentials (Client IDandClient secret). - Click
Authorize.
Note: Even if the button says Authorize, it's really the authentication process.
Authenticating using Postman
When using Postman, you will have to import the Swagger file into a Postman collection as follows:
- Open the API reference on SwaggerHub.
- On the top right, click 'Export', then 'Download API', and select 'YAML Unresolved'. Alternatively, you can directly append '?format=yaml' to the SwaggerHub API URL (for example: https://api.swaggerhub.com/apis/kpn/sms-kpn/1.0.6?format=yaml) and use this link to import the specification into Postman.
- In Postman from the menu click
Fileand clickImport... Choose the YAML file you downloaded in the previous step. A new collection will be added. - Select
Get Access Tokenfrom the collection. - Make sure the right environment is selected, corresponding to the API.
- Edit the environment variables
client_idandclient_secret, using your credentials (Client IDandClient secret). - Check the response code and message.
- Press the
Sendbutton to get an access token.
Note: Request variables are no longer linked to an environment, but to the collection.